 Ransomware is malicious software designed to encrypt computer files. As a result, it will deny or delete access to the files until victims pay a fee. Essentially, the hacker will hold the data hostage until the company pays the ransom.
Ransomware is malicious software designed to encrypt computer files. As a result, it will deny or delete access to the files until victims pay a fee. Essentially, the hacker will hold the data hostage until the company pays the ransom.
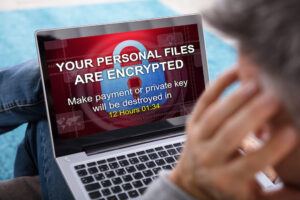
Many ransomware attacks come as an attachment on an email. The attack may cause a computer to freeze and display a ransom message, instructions for payment, and a countdown clock on the screen. The impact can be financially devastating if the demands are high or the data taken hostage is lost.
The threat of ransomware is a problem that’s difficult to wipe completely. Unfortunately, it only takes one wrong click or download to give cybercriminals the access they need to take control of your data entirely.
How Do Ransomware Attacks Happen?
Since the first recorded incident in the 1980s, ransomware has continued to advance. Even high-profile organizations such as healthcare providers, hospitals, and school districts are susceptible to attacks. Ransomware can appear through various channels and in different forms. Common ways include email links, PDFs, Word documents, or links to malicious websites.
Ransomware software can encrypt documents, data, photos, and other essential files. As a result, the ransomware will cause the files to be inaccessible without a key. These attacks can quickly work their way up a network of computers and devastate an entire organization. For example, a ransomware incident in 2017 impacted ~4000 servers and 45,000 PCs along with ~2500 applications over two weeks.
One of the most infamous ransomware attacks was the Maze Ransomware Attack. It spread through multiple channels, including “look-a-like cryptocurrency sites and malspam campaigns impersonating government agencies and well-known security vendors.”
The Impact of Ransomware Attacks
Ransomware continues to be a growing threat to organizations. The results of the attacks are financially devastating for companies. Additionally, attackers will request the ransom payment in bitcoins. Which is a digital currency that makes it impossible to track back to the owner. Therefore, anonymity of it makes it difficult to track down and charge the criminals.
By the end of 2020, projected ransomware costs to reach $20 billion in payments to cybercriminals. Specifically, the Maze ransomware attack targeted an IT services supplier, Cognizant. The attack cost between $50 million and $70 million as they worked to restore their computer systems fully.
Recovery From a Ransomware Attack
Ransomware can take out a whole organization. Even if external backups are available, it still takes a few days to get everything back up and running.
These attacks can result in a loss of customers because of the time wasted paying back the criminals, the system going offline, and projects coming to a halt. (Note: some experts advise against paying the ransom.)
The consequences of not regaining the encrypted data might have a severe financial impact on an organization. There is no guarantee the attackers will ever send the decryption key after meeting their demands. The attacker may runoff, or the demands may continue to increase.
It’s best to take action before any of this can happen. With Wahaya IT, we provide preventative tactics to protect against ransomware.
Methods to Protect Against Ransomware
To avoid a ransomware attack in the first place, here are some steps you can take to remain vigilant and prepared:
Regular Security Software Updates – Keep all software programs up to date and working correctly on all employee devices. Developers will often patch vulnerabilities with new updates.
Employee Training – Internal threats are one the largest sources of security breaches. For this reason, keep employees informed on security best practices. As a result, employees can be aware of these types of attacks.
Cloud and Physical Backups – Backups are the most straightforward method to restore systems if you suffer an attack. In most cases, you can wipe your computer and avoid paying a fee. Always have regular backups of essential files on the cloud and an external hard drive.
Use Pop-up Blockers – Install pop-up blocker software to protect against unwanted pop-ups. Such as browser hijacks, malware, and adware.
Partner with Wahaya IT – Find the proper data protection and backup solutions for your organization.
Prepare As If A Ransomware Attack Could Happen at Any Moment
Ransomware is not that much different from other cyber attacks. They can happen within seconds and leave a devastating impact on those affected.
No single method of protection is foolproof. However, without any protections in place, an organization is very vulnerable to an attack.
Find the right IT solutions to stop ransomware in its tracks. The experts at Wahaya IT can help. Wahaya IT can pair you up with the right security solutions for your organization. For example, we provide employee awareness training and regular backup tools.
Contact Wahaya IT to learn more about our cybersecurity and cloud solutions.