Many people worry about someone hacking their computers. But they're not thinking about their wireless printer getting breached. It's a tool that...
Tech Tips
6 Things You Should Do to Handle Data Privacy Updates
Once data began going digital, authorities realized a need to protect it. Thus, data privacy rules and regulations were created to address cyber...
What Is App Fatigue & Why Is It a Security Issue?
The number of apps and web tools employees use regularly continues to increase. Most departments have about 40-60 different digital tools that they...
How to Use the New Virtual Appointments in Microsoft Teams
Scheduling appointments is a common activity. For example, salespeople often set up virtual meetings to answer questions about a product. Software...
These Everyday Objects Can Lead to Identity Theft
You wouldn't think a child's toy could lead to a breach of your data. Or is the trash can sitting outside a treasure trove for an identity thief...
Think Twice Before Using Lensa AI & Other Self-Portrait Apps
It's a common theme. You begin seeing these amazing CGI images of your friends on Facebook or Instagram. You think, "How can I make one?" Filters...
8 Reasons Every Company Is Now a Technology Company
Whether you sell shoes or run an accounting firm, you need technology to operate. Today’s companies aren’t just in the business of selling their...
Data Backup Is Not Enough, You Also Need Data Protection
The need to back up data has been around since floppy disks. Data loss happens due to viruses, hard drive crashes, and other mishaps. Most people...
6 Steps to Effective Vulnerability Management for Your Technology
Technology vulnerabilities are an unfortunate side effect of innovation. When software companies push new updates, the code often has weaknesses....
Smart Tips to Keep Your Online Banking Account Safe
There are a lot of things that have changed since the invention of the internet. One of these is how we bank and access our accounts. You used to...
Is That Really a Text from Your CEO… or Is It a Scam?
Imagine you're going about your day when suddenly you receive a text from the CEO. The head of the company is asking for your help. They're out...
Pros & Cons of Tracking Your Employee’s Digital Movement
Since the pandemic, employers around the world have needed to change. They've had to shift how their employees operate. Remote work is very much...
AI and the Terms You Need to Know
The whole world is suddenly talking about Artificial Intelligence. From Alexa in your kitchen to Siri on your phone, AI is already all around us,...
6 Ways to Prevent Misconfiguration and Avoid Cloud Breaches
Misconfiguration of cloud solutions is often overlooked when companies plan cybersecurity strategies. Cloud apps are typically quick and easy to...
7 Most Exciting App Announcements at Microsoft Ignite 2022
If you follow Microsoft products, then you may know about Microsoft Ignite. Held annually, it generates many exciting updates and announcements in...
Have You Had Data Exposed in One of These Recent Data Breaches
Make Sure Your Router is Secure There’s a reason that browsers like Edge have added breached password notifications. Data breaches are an...
8 Tech Checks to Make Before You Travel
Our technology inevitably comes with us when we travel. Most of us won't even travel to the end of the block without our smartphones. Not having...
2023 Trends in Data Privacy That Could Impact Your Compliance
Data privacy has been a growing requirement ever since the internet age began. So much personal information is flying around through computer...
When Did You Last Have an IT Health Check?
How’s the January health kick going? Lots of us take our health seriously – once a year, anyway – and it’s good to think about whether you’ve been...
Don’t Set Yourself Up to Fail: Tips for Safer Home Security Setups
The global home security market has been growing by leaps and bounds. By 2026, experts expect the need to expand at 20.1%. This is on top of an...
Cyberattacks to Watch Out for in 2023?
The new year has just begun, and it's a time of renewal as we plan for the possibilities to come in 2023. It's also a time when you need to prepare...
7 Apps That Can Help You Improve Customer Experience in 2023
Paying attention to your customer experience directly impacts your bottom line. Companies that are “customer-centric” are 60% more profitable than...
What to Include in a Year-end Technology Review
When the year is coming to a close, it’s the perfect time to plan for the future. Most businesses begin the year with the hope of growing and...
Tips for Overcoming Barriers to a Smooth BYOD Program
BYOD (bring your own device) is a concept that took hold after the invention of the smartphone. When phones got smarter, software developers began...
Simple Setup Checklist for Microsoft Teams
Microsoft Teams is a lot of things. It's a video conferencing tool, a team messaging channel, and a tool for in-app co-authoring, to name a few....
Why you will not be fine on this Cloud9
Wahaya IT works to protect our clients from online security threats. Cloud9 As part of our service, we always advise our clients to install software...
What Are the Most Helpful VoIP Features for Small Businesses?
Five or six years ago, VoIP was still considered a "different" business phone system. One that wasn't the norm. But the pandemic changed that way of...
A Simple Guide to Follow for Better Endpoint Protection
Endpoints make up much of a company's network and IT infrastructure. This collection of computers, mobile devices, servers, smart gadgets, and other...
9 Urgent Security Tips for Online Holiday Shopping
The holiday shopping season is taking off. Unfortunately, this means that scammers have also revved up their engines. They're primed and ready to...
Watch Out for Reply-Chain Phishing Attack
Phishing. You can't read an article on cybersecurity without it coming up. That's because phishing is still the number one delivery vehicle...
Digital Workplace and the 5 Mistakes Companies Are Making
The pandemic has been a reality that companies around the world have shared. It required major changes in how they operate. The status quo of having...
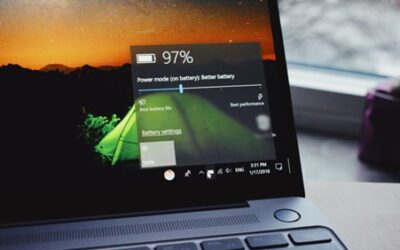
Get More Unplugged Laptop Time with These Battery-Saving Hacks
One of the big draws of a laptop computer is that you can use it anywhere. You don't need to have it plugged in all the time because it has an...
7 Pro Tips for Microsoft 365
Microsoft 365 is the most popular of all major office productivity software. It has 48.8% of the global market share, just edging out Google's apps...